Scams
$90,000/year, full home office, and 30 days of paid leave, and all for a job as a junior data analyst – unbelievable, right? This and many other job offers are fake though – made just to ensnare unsuspecting victims into giving up their data.
06 Jun 2024
•
,
5 min. read

Seeking a job these days can be quite difficult, with many employers looking to freeze hiring or not hire as much as they used to. Plus, with the numerous recent layoffs, more job seekers are on the market than before.
Even so, this does not mean that firms stop advertising for jobs completely – frozen job positions can remain up as “ghost job” offers, despite a company not looking for anyone in particular.
However, the issue is that these positions are also joined by fake posts claiming to be offers from legitimate companies, overstuffing job boards. What’s more, these adverts can seem very authentic, as scammers often go as far as to completely construct the persona and professional life of a recruiter or HR person, sometimes stealing actual online data of people to do so.
Why? As always, the end goal of such scams is to use the collected data to achieve some form of monetary or other gain. And although job scammers can be cunning, they are not impossible to spot.
Constructing fake identities
As outlined in a previous WeLiveSecurity blog by Daniel Cunha Barbosa, people often reveal too much about themselves online, especially on sites such as LinkedIn, which serves both as a professional social media service and as a job board. This can make it easier for crooks to harvest data – be it by purchasing leaked account credentials or by doing a bit of web scraping.
For example, open-source intelligence (OSINT) tools can easily help collect data from people’s online profiles and activities. Software such as Maltego helps uncover information about people or companies online, enabling anyone to connect and map out relationships between websites, accounts, emails, locations, and more.
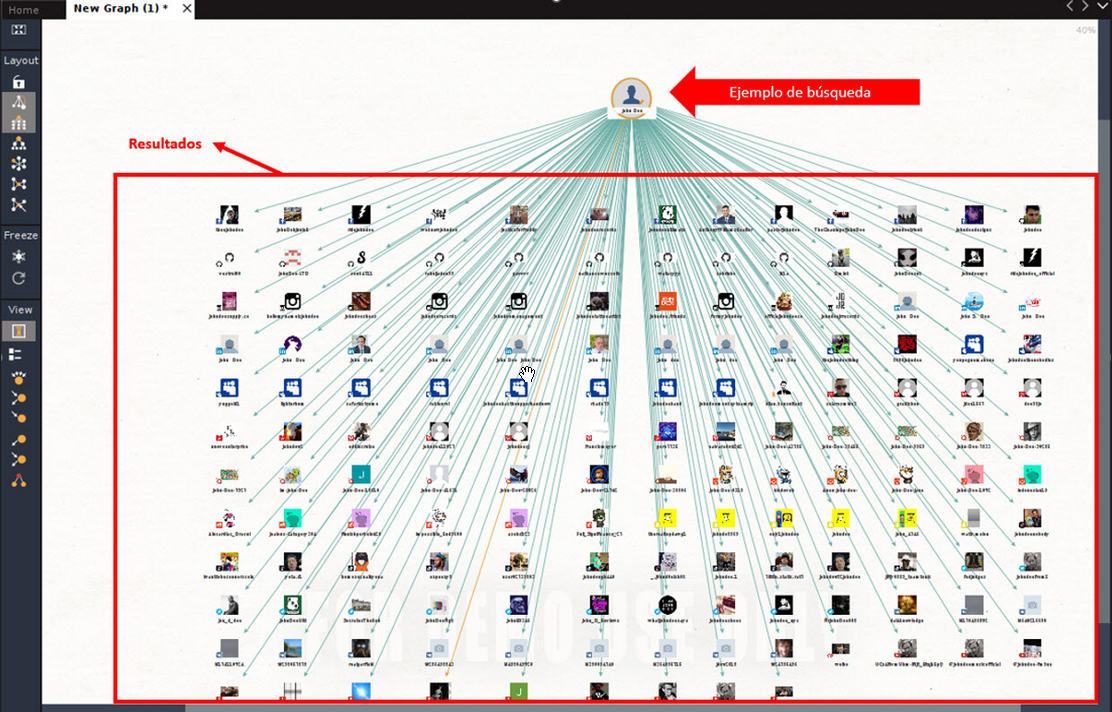
Information that Maltego can map out. See how vast the connections to just a single person can be. (Source: Sol González/WeLiveSecurity)
As a result, constructing profiles intended to lure unsuspecting users to fake jobs for further data collection to commit more crimes, such as business email compromise or various social engineering attacks, becomes easier than ever.
On the other hand, with OSINT tools, people can check how exposed they are online, so they also have a positive application, especially for security practitioners, who can use them to uncover information about potential threats that can upset the security postures of those they protect.
Spotting a fake job posting
What does a fraudulent job post look like? It depends, as fake recruiters might message job seekers directly, and include a malicious link or attachment inside the message/email. These are also joined by fake job posts on recruitment boards, making the positions look more real.
Moreover, early during the application process, fakes can go so far as to request bank account information or social security numbers, which should always ring an alarm bell in anyone’s mind.
So, to confirm whether you are about to interact with a genuine offer, your best bet is to check:
- Whether the company and person exist – legal business name, address, registration, online presence, and potential news reports.
- Social media profiles of the business/recruiter, and look for grammar mistakes, weird date cutoffs on their posts, and a lack of constant online activity (fake profiles might not have a long-term regular online presence).
- If they have reactions from real people, recommendations from previous employers and colleagues, certifications, genuine reactions of their own on the posts of others, etc.
- Their other job board posts or past activity – the more posts they have on other boards, the more likely they are to be real. If you can, also check their posts on local boards, but this does not guarantee authenticity.
Small mistakes can also make a difference. Crooks often recreate company work pages to seem more genuine, but these pages can also have some discernible qualities:
- Website security: Fake websites might lack the HTTPS certificate, which can be a sign of an insecure, malicious site.
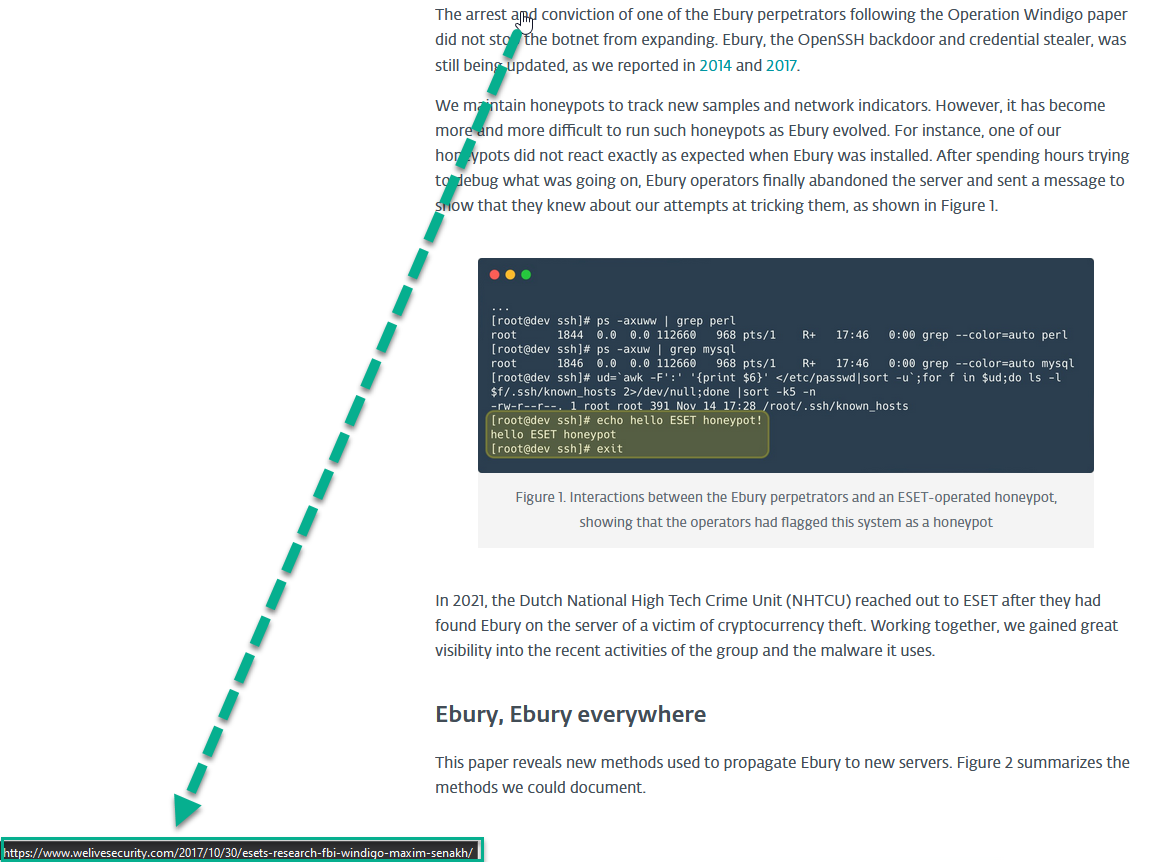
- Links: These can have many tell-tale signs, like misspellings. Plus, links do not have to take you to the same location as specified – hence before you click, hover over the link and check the intended location in the tooltip on the bottom left of your browser window as seen in the image below.
- Suspicious asks: No company will ask for your bank account number, social security number, ID, or similar while interviewing for a job. Unless you are already an employee (and have met verified HR representatives), providing such information is a no-go.
- Typos: Faked websites can have lots of typos or grammar mistakes, stylistic issues, or deliberate character changes that might be unnoticeable at first (using “0racle” instead of “Oracle,” for example).
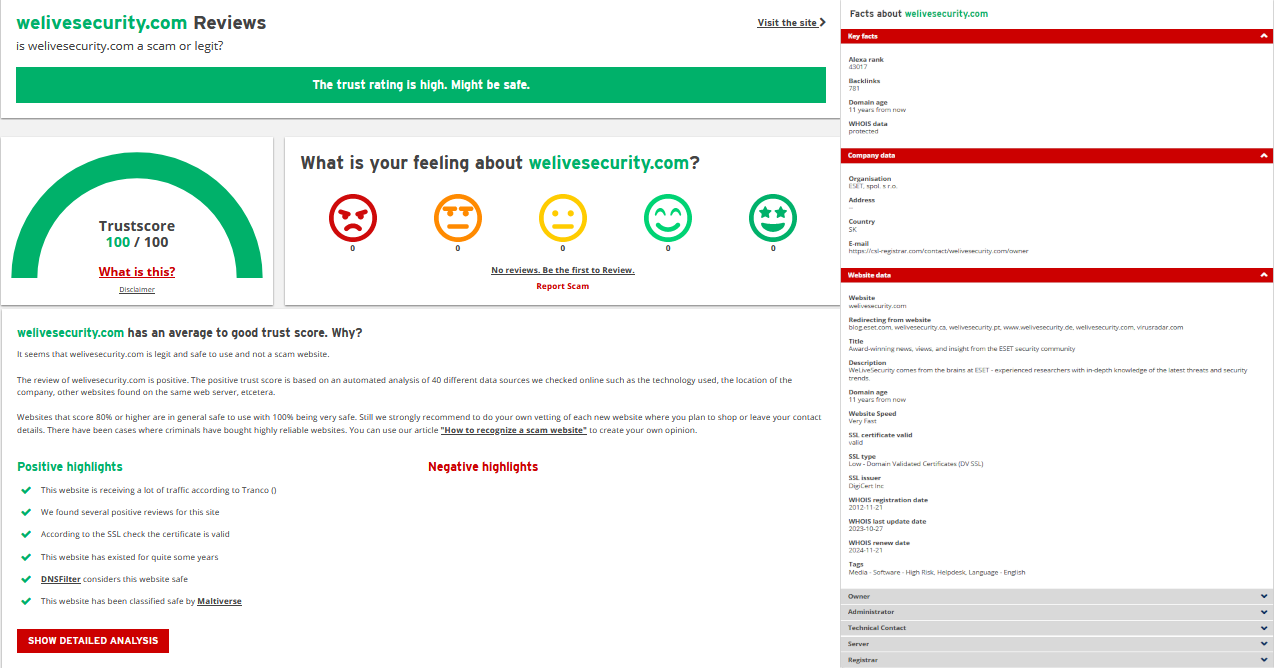
- Reputation: When possible, run a quick check of the domain on a site like who.is or ScamAdviser.com, which will give you useful information about the registration of the site, its age, and more.
Some basic guidance
Any discussion of protection against job scams needs to cover more than just one angle.
First, to not fall victim to identity fraud, restrict your privacy settings on job boards (or social media in general) if you can, and never willingly present personally identifiable information online, which includes any account with public visibility. As previously mentioned, doing so will make it much easier to construct a profile on you using OSINT tools and web scrapers.
On LinkedIn, for example, you can set up whether you want your profile to be public or private (only visible to other LI users), as well as who can see your full last name and other information. You can find out more about this in an article by André Lameiras.
Second, never give away your data without verifying your potential employer. It is quite easy to fall prey to a fake job posting, but a tell-tale sign can be as simple as a barebones job advert or spotty online presence.
Third, be wary of random emails or messages with job offers from, unverified or untrustworthy-looking accounts.
Lastly, if an offer seems too enticing (giving an above-average wage while requiring next to no experience, for example), it is likely to be a scam.
All in all, the likelihood of anyone encountering a fake job posting is high, so pay attention and try to stay cyber secure for as long as possible.

