Unidentified threat actors breached a server running an unpatched, 11-year-old version of Adobe’s ColdFusion 9 software in minutes to remotely take over control and deploy file-encrypting Cring ransomware on the target’s network 79 hours after the hack.
The server, which belonged to an unnamed services company, was used to collect timesheet and accounting data for payroll as well as to host a number of virtual machines, according to a report published by Sophos and shared with The Hacker News. The attacks originated from an internet address assigned to the Ukrainian ISP Green Floid.
“Devices running vulnerable, outdated software are low-hanging-fruit for cyberattackers looking for an easy way into a target,” Sophos principal researcher Andrew Brandt said. “The surprising thing is that this server was in active daily use. Often the most vulnerable devices are inactive or ghost machines, either forgotten about or overlooked when it comes to patching and upgrades.”
The British security software firm said the “rapid break-in” was made possible by exploiting an 11-year-old installation of Adobe ColdFusion 9 running on Windows Server 2008, both of which have reached end-of-life.
Upon gaining an initial foothold, the attackers used a wide range of sophisticated methods to conceal their files, inject code into memory, and cover their tracks by overwriting files with garbled data, not to mention disarm security products by capitalizing on the fact that tamper-protection functionalities were turned off.
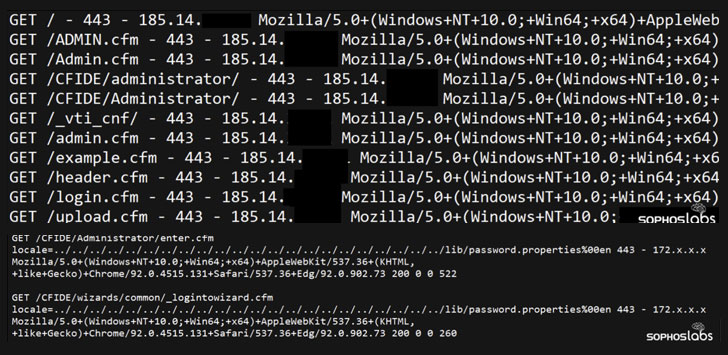
Specially, the adversary took advantage of CVE-2010-2861, a set of directory traversal vulnerabilities in the administrator console in Adobe ColdFusion 9.0.1 and earlier that could be abused by remote attackers to read arbitrary files, such as those containing administrator password hashes (“password.properties”).
In the next stage, the bad actor is believed to have exploited another vulnerability in ColdFusion, CVE-2009-3960, to upload a malicious Cascading Stylesheet (CSS) file to the server, consequently using it to load a Cobalt Strike Beacon executable. This binary, then, acted as a conduit for the remote attackers to drop additional payloads, create a user account with admin privileges, and even disable endpoint protection systems and anti-malware engines like Windows Defender, before commencing the encryption process.
“This is a stark reminder that IT administrators benefit from having an accurate inventory of all their connected assets and cannot leave out-of-date critical business systems facing the public internet,” Brandt said. “If organizations have these devices anywhere on their network, they can be sure that cyberattackers will be attracted to them.”