A newly disclosed vulnerability affecting Intel processors could be abused by an adversary to gain access to sensitive information stored within enclaves and even run arbitrary code on vulnerable systems.
The vulnerability (CVE-2021-0186, CVSS score: 8.2) was discovered by a group of academics from ETH Zurich, the National University of Singapore, and the Chinese National University of Defense Technology in early May 2021, who used it to stage a confidential data disclosure attack called “SmashEx” that can corrupt private data housed in the enclave and break its integrity.
Introduced with Intel’s Skylake processors, SGX (short for Software Guard eXtensions) allows developers to run selected application modules in a completely isolated secure compartment of memory, called an enclave or a Trusted Execution Environment (TEE), which is designed to be protected from processes running at higher privilege levels like the operating system. SGX ensures that data is secure even if a computer’s operating system has been tampered with or is under attack.
“For normal functioning, the SGX design allows the OS to interrupt the enclave execution through configurable hardware exceptions at any point,” the researchers outlined. “This feature enables enclave runtimes (e.g., Intel SGX SDK and Microsoft Open Enclave) to support in-enclave exception or signal handling, but it also opens up enclaves to re-entrancy bugs. SmashEx is an attack which exploits enclave SDKs which do not carefully handle re-entrancy in their exceptional handling safely.”
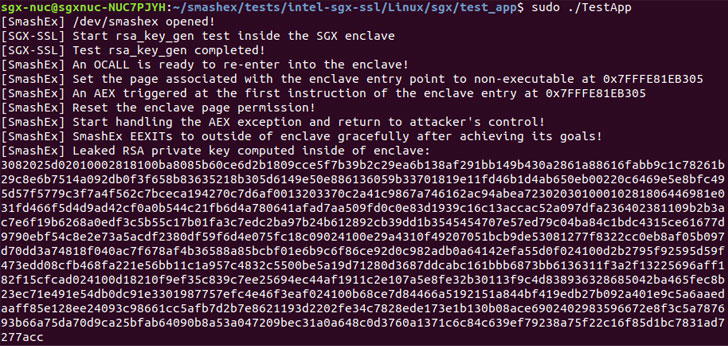
It’s worth noting that an enclave may also have Outside Calls, or OCALLS, which allow enclave functions to call out to the untrusted application and then return to the enclave. But when the enclave is also handling in-enclave exceptions (e.g., timer interrupt or division-by-zero), the vulnerability provides a brief window for a local attacker to hijack the control flow of execution by injecting an asynchronous exception immediately after the enclave is entered.
Armed with this capability, the adversary can then corrupt the in-enclave memory to leak sensitive data such as RSA private keys or execute malicious code.
Since SmashEx affects runtimes that support in-enclave exception handling, the researchers noted that “such OCALL return flow and the exception handling flow should be written with care to ensure that they interleave safely,” and that “when the OCALL return flow is interrupted, the enclave should be in a consistent state for the exception handling flow to progress correctly, and when the exception handling flow completes, the enclave state should also be ready for the enclave to resume.”
Intel has since released software updates to mitigate this vulnerability with SGX SDK versions 2.13 and 2.14 for Windows and Linux respectively. Microsoft, for its part, addressed the issue (CVE-2021-33767) in its July 2021 Patch Tuesday updates with Open Enclave version 0.17.1 of the SDK. The research team’s findings are expected to be presented next month at the ACM Conference on Computer and Communications Security.
“Asynchronous exception handling is a commodity functionality for real-world applications today, which are increasingly utilizing enclaves,” the researchers said, adding the research highlights “the importance of providing atomicity guarantees at the OS-enclave interface for such exceptions.”