A new cyber mercenary hacker-for-hire group dubbed “Void Balaur” has been linked to a string of cyberespionage and data theft activities targeting thousands of entities as well as human rights activists, politicians, and government officials around the world at least since 2015 for financial gain while lurking in the shadows.
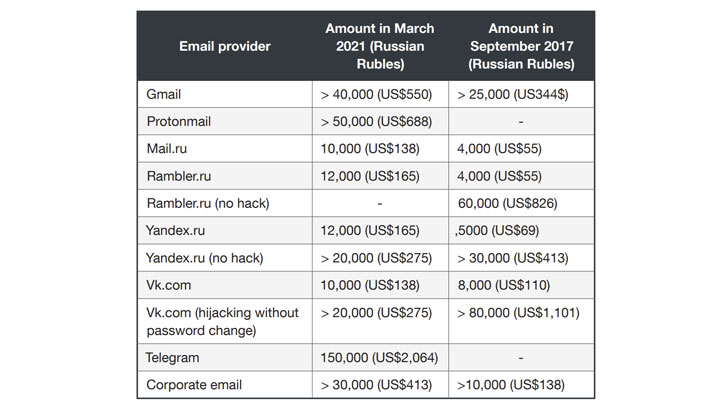
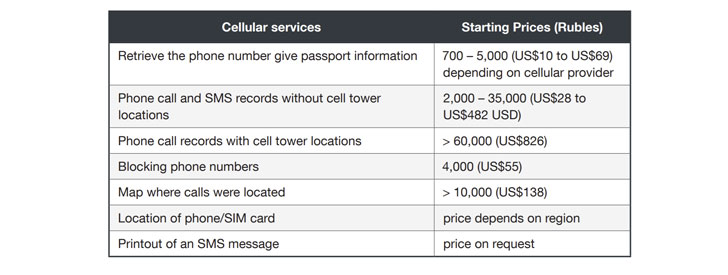
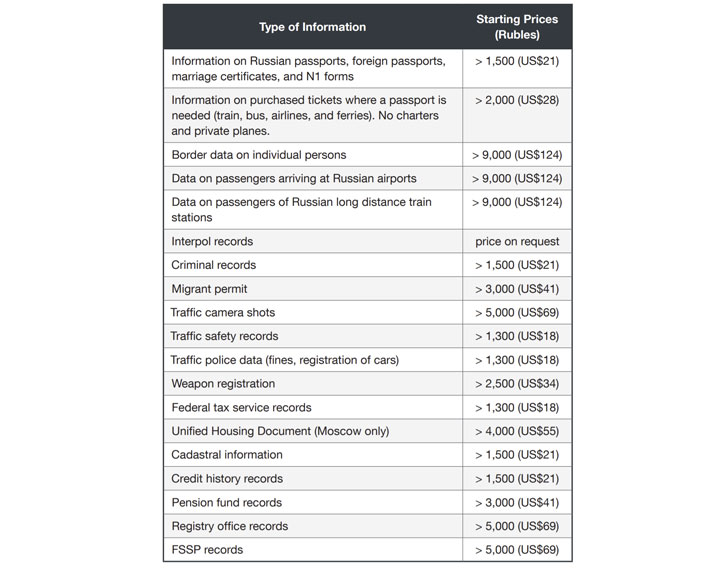
Named after a many-headed dragon from Romanian folklore, the adversary has been unmasked advertising its services in Russian-speaking underground forums dating all the way back to 2017 and selling troves of sensitive information such as cell tower phone logs, passenger flight records, credit reports, banking data, SMS messages, and passport details. The threat actor calls itself “Rockethack.”
“This hacker-for-hire group does not operate out of a physical building, nor does it have a shiny prospectus that describes its services,” Trend Micro researcher Feike Hacquebord said in a newly published profile of the collective.
“The group does not try to wriggle out of a difficult position by justifying its business, nor is it involved in lawsuits against anybody attempting to report on their activities. Instead, this group is quite open about what it does: breaking into email accounts and social media accounts for money,” Hacquebord added.
Besides gaining near unanimous positive reviews on the forums for its ability to offer quality information, Void Balaur is also believed to have focused on cryptocurrency exchanges by creating numerous phishing sites to trick cryptocurrency exchange users in order to gain unauthorized access to their wallets. What’s more, the mercenary collective has deployed an information stealer named Z*Stealer and Android malware such as DroidWatcher against its targets.
Void Balaur’s intrusion set has been observed deployed against a wide range of individuals and entities, including journalists, human rights activists, politicians, scientists, doctors working in IVF clinics, genomics and biotechnology companies, and telecom engineers. Trend Micro said it unearthed over 3,500 email addresses the group set its aim on.
Most of the group’s targets are said to be located in Russia and other neighboring countries like Ukraine, Slovakia, and Kazakhstan, with victims also located in the U.S., Israel, Japan, India, and European nations. Assaulted organizations run the gamut from telecom providers, satellite communication corporations, and fintech firms to ATM machine vendors, point-of-sale (PoS) vendors, and biotech companies.
“Void Balaur goes after the most private and personal data of businesses and individuals then sells that data to whomever wants to pay for it,” the researchers said. The reason why these individuals and entities were targeted remains unknown as yet.
It’s not immediately clear how sensitive phone and email records are acquired from the targets without interaction, although the researchers suspect that the threat actor could have either directly (or indirectly) involved rogue insiders at the concerned companies to sell the data or by compromising accounts of key employees with access to the targeted email mailboxes.
Trend Micro’s deep-dive analysis has also found some common ground with another Russia-based advanced persistent threat group named Pawn Storm (aka APT28, Sofacy, or Iron Twilight), with overlaps observed in the targeted email addresses between the two groups, while also significantly differing in a number of ways, including Void Balaur’s modus operandi of striking cryptocurrency users and their operational hours.
If anything, the development once again highlights the rampantly growing illicit mercenary-related activities in cyberspace and the demand for such services, what with a number of operations — BellTroX (aka Dark Basin), Bahamut, CostaRicto, and PowerPepper — that have been exposed as targeting financial institutions and government agencies in recent months.
To defend against the hacking attacks, it’s recommended to enable two-factor authentication (2FA) via an authenticator app or a hardware security key, rely on apps with end-to-end encryption (E2EE) for email and communications, and permanently delete old, unwanted messages to mitigate the risk of data exposure.
“The reality is that regular internet users cannot easily deter a determined cyber mercenary,” the researchers concluded. “While [advanced offensive tools in a cyber mercenary’s arsenal] might be meant to be used in the fight against terrorism and organized crime, the reality is that they — knowingly or unknowingly — end up in the hands of threat actors who use it against unwitting targets.”