Ransomware groups continue to evolve their tactics and techniques to deploy file-encrypting malware on compromised systems, notwithstanding law enforcement’s disruptive actions against the cybercrime gangs to prevent them from victimizing additional companies.
“Be it due to law enforcement, infighting amongst groups or people abandoning variants altogether, the RaaS [ransomware-as-a-service] groups dominating the ecosystem at this point in time are completely different than just a few months ago,” Intel 471 researchers said in a report published this month. “Yet, even with the shift in the variants, ransomware incidents as a whole are still on the rise.”
Sweeping law enforcement operations undertaken by government agencies in recent months have brought about rapid shifts in the RaaS landscape and turned the tables on ransomware syndicates like Avaddon, BlackMatter, Cl0p, DarkSide, Egregor, and REvil, forcing the actors to slow down or shut down their businesses altogether.
But just as these variants are fading into obscurity, other up-and-coming groups have stepped in to fill the vacuum. Intel 471’s findings have uncovered a total of 612 ransomware attacks between July to September 2021 that can be attributed to 35 different ransomware variants.
Roughly 60% of the observed infections were tied to four variants alone — topped by LockBit 2.0 (33%), Conti (15.2%), BlackMatter (6.9%), and Hive (6%) — and primarily impacted manufacturing, consumer and industrial products, professional services and consulting, and real estate sectors.
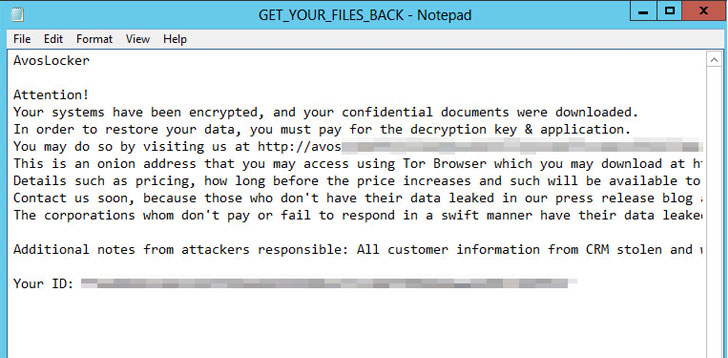
Avos Locker is one among the many such cartels that have not only witnessed a surge in attacks, but have also adopted new tactics to pursue their financially motivated schemes, chief among them being the ability to disable endpoint security products on the targeted systems and boot into Windows Safe Mode to execute the ransomware. Also installed is the AnyDesk remote administration tool to maintain access to the machine while running in Safe Mode.
“The reason for this is that many, if not most, endpoint security products do not run in Safe Mode — a special diagnostic configuration in which Windows disables most third-party drivers and software, and can render otherwise protected machines unsafe,” SophosLabs principal security researcher, Andrew Brandt, said. “The techniques deployed by Avos Locker are simple yet clever, with attackers ensuring that the ransomware has the best chance of running in Safe Mode and allowing the attackers to retain remote access to the machines throughout the attack.”
Hive’s RaaS program, for its part, has been dubbed “aggressive” for its use of pressure tactics to make victim organizations pay ransoms, with Group-IB linking the strain to attacks on 355 companies as of October 16 since it emerged on the landscape in late June 2021. Meanwhile, Russian-language ransomware group Everest is taking its extortion tactics to the next level by threatening to sell off access to targeted systems if their demands aren’t met, NCC Group said.
“While selling ransomware-as-a-service has seen a surge in popularity over the last year, this is a rare instance of a group forgoing a request for a ransom and offering access to IT infrastructure — but we may see copycat attacks in 2022 and beyond,” the U.K.-based cybersecurity company pointed out.
What’s more, a relatively new ransomware family dubbed Pysa (aka Mespinoza) has unseated Conti as one of the top ransomware threat groups for the month of November alongside LockBit 2.0. The ransomware witnessed a 50% increase in the number of targeted companies and a 400% spike in attacks against government-sector systems when compared to the month of October.
“While law enforcement around the world has gotten more aggressive in their efforts to arrest those behind attacks, developers are still easily shutting down popular variants, laying low, and coming back with finely-tuned malware used by themselves as well as affiliates,” Intel 471 researchers said. “As long as the developers can remain in countries where they are granted safe harbor, the attacks will continue, albeit with different variants.”