An ongoing crypto mining campaign has upgraded its arsenal while adding new defense evasion tactics that enable the threat actors to conceal the intrusions and fly under the radar, new research published today has revealed.
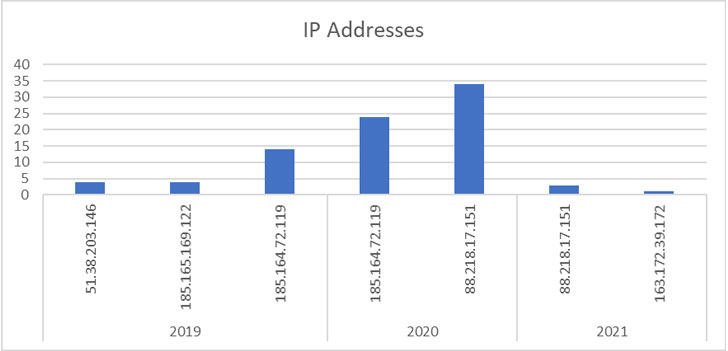
Since first detected in 2019, a total of 84 attacks against its honeypot servers have been recorded to date, four of which transpired in 2021, according to researchers from DevSecOps and cloud security firm Aqua Security, who have been tracking the malware operation for the past three years. That said, 125 attacks have been spotted in the wild in the third quarter of 2021 alone, signaling that the attacks have not slowed down.
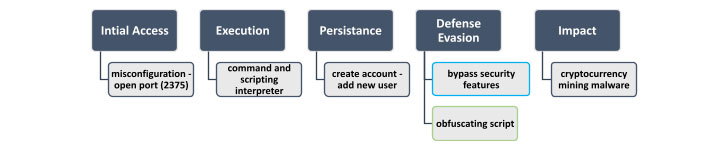
Initial attacks involved executing a malicious command upon running a vanilla image named “alpine:latest” that resulted in the download of a shell script named “autom.sh.”
“Adversaries commonly use vanilla images along with malicious commands to perform their attacks, because most organizations trust the official images and allow their use,” the researchers said in a report shared with The Hacker News. “Over the years, the malicious command that was added to the official image to carry out the attack has barely changed. The main difference is the server from which the shell script autom.sh was downloaded.”
The shell script initiates the attack sequence, enabling the adversary to create a new user account under the name “akay” and upgrade its privileges to a root user, using which arbitrary commands are run on the compromised machine with the goal of mining cryptocurrency.
While early stages of the campaign in 2019 featured no special techniques to hide the mining activity, later versions show the extreme measures its developers have taken to keep it invisible to detection and inspection, chief among them being the ability to disable security mechanisms and retrieve an obfuscated mining shell script that was Base64-encoded five times to get around security tools.
Malware campaigns carried out to hijack computers to mine cryptocurrencies have been dominated by multiple threat actors such as Kinsing, which has been found scanning the internet for misconfigured Docker servers to break into the unprotected hosts and install a previously undocumented coin miner strain.
On top of that, a hacking group named TeamTNT has been observed striking unsecured Redis database servers, Alibaba Elastic Computing Service (ECS) instances, exposed Docker APIs, and vulnerable Kubernetes clusters in order to execute malicious code with root privileges on the targeted hosts as well as deploy cryptocurrency-mining payloads and credential stealers. In addition, compromised Docker Hub accounts have also been employed to host malicious images that were then used to distribute cryptocurrency miners.
In recent weeks, security flaws in the Log4j logging library as well as vulnerabilities recently uncovered in Atlassian Confluence, F5 BIG-IP, VMware vCenter, and Oracle WebLogic Servers have been abused to take over machines to mine cryptocurrencies, a scheme known as cryptojacking. Earlier this month, network-attached storage (NAS) appliance maker QNAP warned of cryptocurrency mining malware targeting its devices that could occupy around 50% of the total CPU usage.
“Miners are a low-risk way for cybercriminals to turn a vulnerability into digital cash, with the greatest risk to their cash flow being competing miners discovering the same vulnerable servers,” Sophos senior threat researcher Sean Gallagher noted in an analysis of a Tor2Mine mining campaign, which involves the use of a PowerShell script to disable malware protection, execute a miner payload, and harvest Windows credentials.
“The Autom campaign illustrates that attackers are becoming more sophisticated, continually improving their techniques and their ability to avoid detection by security solutions,” the researchers said. To protect against these threats, it’s recommended to monitor suspicious container activity, perform dynamic image analysis, and routinely scan the environments for misconfiguration issues.