A threat actor with potential links to an Indian cybersecurity company has been nothing if remarkably persistent in its attacks against military organizations based in South Asia, including Bangladesh, Nepal, and Sri Lanka, since at least September 2020 by deploying different variants of its bespoke malware framework.
Slovak cybersecurity firm ESET attributed the highly targeted attack to a hacking group known as Donot Team. “Donot Team has been consistently targeting the same entities with waves of spear-phishing emails with malicious attachments every two to four months,” researchers Facundo Muñoz and Matías Porolli said.
Operating since at least 2016, Donot Team (also known as APT-C-35 and SectorE02) has been linked to a string of intrusions primarily targeting embassies, governments, and military entities in Bangladesh, Sri Lanka, Pakistan, and Nepal with Windows and Android malware.
In October 2021, Amnesty International unearthed evidence tying the group’s attack infrastructure to an Indian cybersecurity company called Innefu Labs, raising suspicions that the threat actor may be selling the spyware or offering a hackers-for-hire service to governments of the region.
While it’s not uncommon for APT groups to re-attack a previously compromised network by deploying stealthier backdoors to cover up their tracks, Donot Team tries a different tack in that it deploys multiple variants of the malware already in its arsenal.
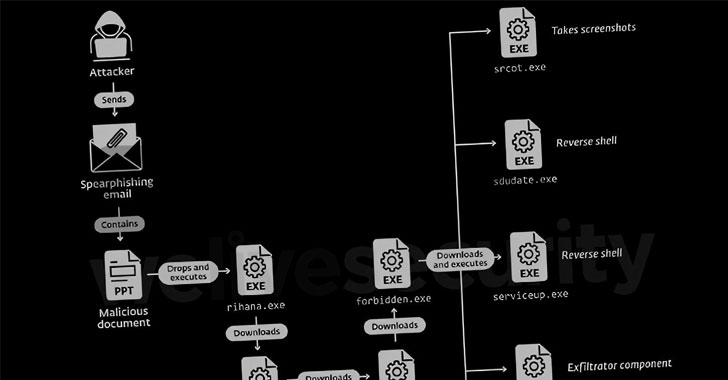
Delivered via weaponized Microsoft Office documents, the so-called yty malware framework is a chain of intermediary downloaders that culminates in the execution of a backdoor, which takes care of retrieving additional components capable of harvesting files, recording keystrokes and screenshots, and deploying reverse shells for remote access.
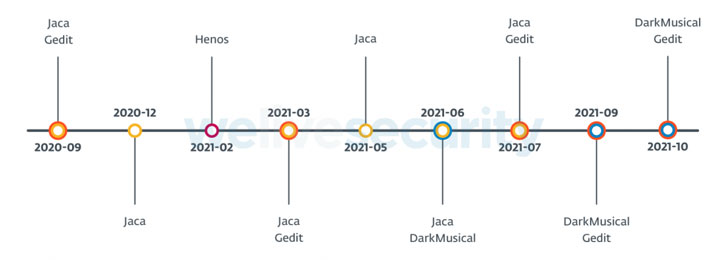
ESET dubbed the new variants of yty, DarkMusical and Gedit, with telemetry data pointing to attacks from a third variant called Jaca from March to July 2021. The first wave of attacks using DarkMusical is said to have occurred in June 2021, while Gedit-related campaigns were observed as early as September 2020, only to pick up the pace a year later.
What’s more, a fourth set of attacks that happened between February and March 2021 targeting military organizations in Bangladesh and Sri Lanka leveraged a modified version of Gedit codenamed Henos.
“Donot Team makes up for its low sophistication with tenacity,” the researchers concluded. “We expect that it will continue to push on regardless of its many setbacks. Only time will tell if the group evolves its current TTPs and malware.”