Social engineering campaigns involving the deployment of the Emotet malware botnet have been observed using “unconventional” IP address formats for the first time in a bid to sidestep detection by security solutions.
This involves the use of hexadecimal and octal representations of the IP address that, when processed by the underlying operating systems, get automatically converted “to the dotted decimal quad representation to initiate the request from the remote servers,” Trend Micro’s Threat Analyst, Ian Kenefick, said in a report Friday.
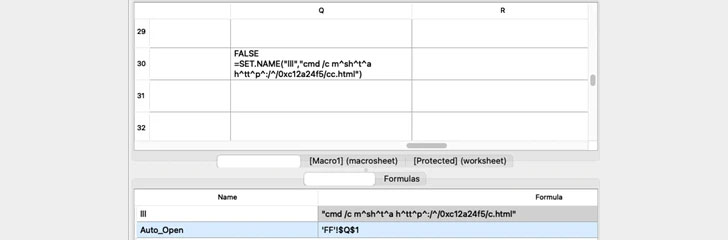
The infection chains, as with previous Emotet-related attacks, aim to trick users into enabling document macros and automate malware execution. The document uses Excel 4.0 Macros, a feature that has been repeatedly abused by malicious actors to deliver malware.
Once enabled, the macro invokes a URL that’s obfuscated with carets, with the host incorporating a hexadecimal representation of the IP address — “h^tt^p^:/^/0xc12a24f5/cc.html” — to execute an HTML application (HTA) code from the remote host.
A second variant of the phishing attack follows the same modus operandi, the only difference being that the IP address is now coded in the octal format — “h^tt^p^:/^/0056.0151.0121.0114/c.html”.
“The unconventional use of hexadecimal and octal IP addresses may result in evading current solutions reliant on pattern matching,” Kenefick said. “Evasion techniques like these could be considered evidence of attackers continuing to innovate to thwart pattern-based detection solutions.”
The development comes amid renewed Emotet activity late last year following a 10-month-long hiatus in the wake of a coordinated law enforcement operation. In December 2021, researchers uncovered evidence of the malware evolving its tactics to drop Cobalt Strike Beacons directly onto compromised systems.
The findings also arrive as Microsoft revealed plans to disable Excel 4.0 (XLM) Macros by default to safeguard customers against security threats. “This setting now defaults to Excel 4.0 (XLM) macros being disabled in Excel (Build 16.0.14427.10000),” the company announced last week.