An advanced persistent threat (APT) group operating with objectives aligned with the Chinese government has been linked to an organized supply chain attack on Taiwan’s financial sector.
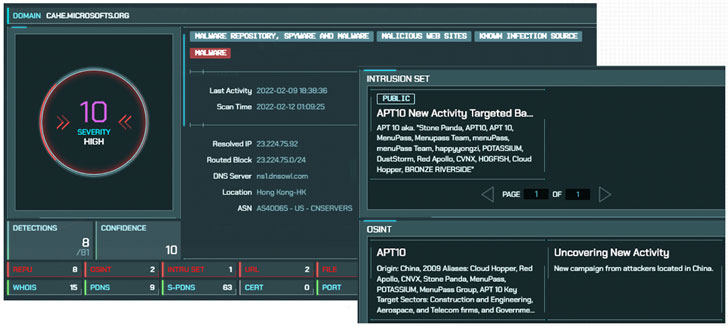
The attacks are said to have first commenced at the end of November 2021, with the intrusions attributed to a threat actor tracked as APT10, also known as Stone Panda, the MenuPass group, and Bronze Riverside, and known to be active since at least 2009.
The second wave of attacks hit a peak between February 10 and 13, 2022, according to a new report published by Taiwanese cybersecurity firm CyCraft, which said the wide-ranging supply chain compromise specifically targeted the software systems of financial institutions, resulting in “abnormal cases of placing orders.”
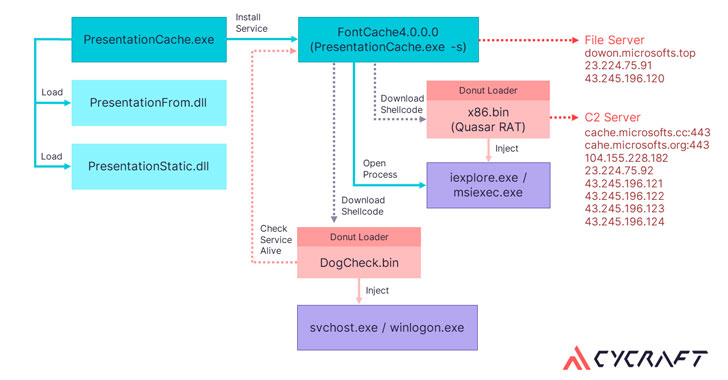
The infiltration activity, codenamed “Operation Cache Panda,” exploited a vulnerability in the web management interface of the unnamed securities software that has a market share of over 80% in Taiwan, using it to deploy a web shell that acts as a conduit for implanting the Quasar RAT on the compromised system with the goal of stealing sensitive information.
Quasar RAT is a publicly available open-source remote access trojan (RAT) written in .NET. Its features include capturing screenshots, recording webcam, editing registry, keylogging, and stealing passwords. In addition, the attacks leveraged a Chinese cloud file sharing service called wenshushu.cn to download auxiliary tools.
The disclosure comes as Taiwan’s Parliament, the Executive Yuan, unveiled draft amendments to national security laws aimed at combating Chinese economic and industrial espionage efforts. To that end, unapproved use of critical national technologies and trade secrets outside of the country could carry up to a 12-year prison sentence.
Furthermore, individuals and organizations that have been entrusted or subsidized by the Taiwanese government to conduct operations involving critical national technologies are expected to secure prior government approval for any trips to China, failing which could incur monetary fines of up to NT$10 million (~US$359,000).