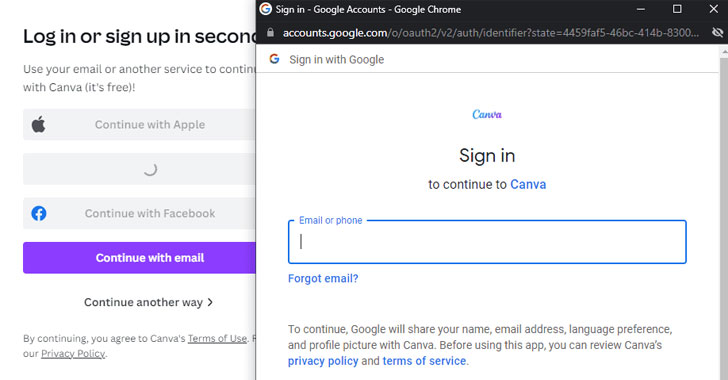
A novel phishing technique called browser-in-the-browser (BitB) attack can be exploited to simulate a browser window within the browser in order to spoof a legitimate domain, thereby making it possible to stage convincing phishing attacks.
According to penetration tester and security researcher, who goes by the handle mrd0x_, the method takes advantage of third-party single sign-on (SSO) options embedded on websites such as “Sign in with Google” (or Facebook, Apple, or Microsoft).
While the default behavior when a user attempts to sign in via these methods is to be greeted by a pop-up window to complete the authentication process, the BitB attack aims to replicate this entire process using a mix of HTML and CSS code to create an entirely fabricated browser window.
“Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it’s basically indistinguishable,” mrd0x_ said in a technical write-up published last week. “JavaScript can be easily used to make the window appear on a link or button click, on the page loading etc.”
While this method significantly makes it easier to mount effective social engineering campaigns, it’s worth noting that potential victims need to be redirected to a phishing domain that can display such a fake authentication window for credential harvesting.
“But once landed on the attacker-owned website, the user will be at ease as they type their credentials away on what appears to be the legitimate website (because the trustworthy URL says so),” mrd0x_ added.