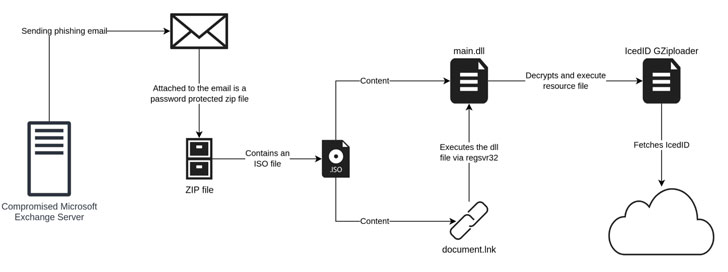
A new email phishing campaign has been spotted leveraging the tactic of conversation hijacking to deliver the IceID info-stealing malware onto infected machines by making use of unpatched and publicly-exposed Microsoft Exchange servers.
“The emails use a social engineering technique of conversation hijacking (also known as thread hijacking),” Israeli company Intezer said in a report shared with The Hacker News. “A forged reply to a previous stolen email is being used as a way to convince the recipient to open the attachment. This is notable because it increases the credibility of the phishing email and may cause a high infection rate.”
The latest wave of attacks, detected in mid-March 2022, is said to have targeted organizations within energy, healthcare, law, and pharmaceutical sectors.
IceID, aka BokBot, like its counterparts TrickBot and Emotet, is a banking trojan that has evolved to become an entry point for more sophisticated threats, including human-operated ransomware and the Cobalt Strike adversary simulation tool.
It’s capable of connecting to a remote server and downloading next-stage implants and tools that allow attackers to carry out follow-on activities and move laterally across affected networks to distribute additional malware.
In June 2021, enterprise security firm Proofpoint disclosed an evolving tactic in the cybercrime landscape wherein initial access brokers were observed infiltrating target networks via first-stage malware payloads such as IcedID to deploy Egregor, Maze, and REvil ransomware payloads.
While earlier IcedID campaigns have taken advantage of website contact forms to send malware-laced links to organizations, the current version of the attacks bank on vulnerable Microsoft Exchange servers to send the lure emails from a hijacked account, indicating a further evolution of the social engineering scheme.
“The payload has also moved away from using Office documents to the use of ISO files with a Windows LNK file and a DLL file,” researchers Joakim Kennedy and Ryan Robinson said. “The use of ISO files allows the threat actor to bypass the Mark-of-the-Web controls, resulting in execution of the malware without warning to the user.”
The idea is to send fraudulent replies to an already existing email thread plundered from the victim’s account by using the compromised individual’s email address to make the phishing emails appear more legitimate.
“The use of conversation hijacking is a powerful social engineering technique that can increase the rate of a successful phishing attempt,” the researchers concluded. “By using this approach, the email appears more legitimate and is transported through the normal channels which can also include security products.”