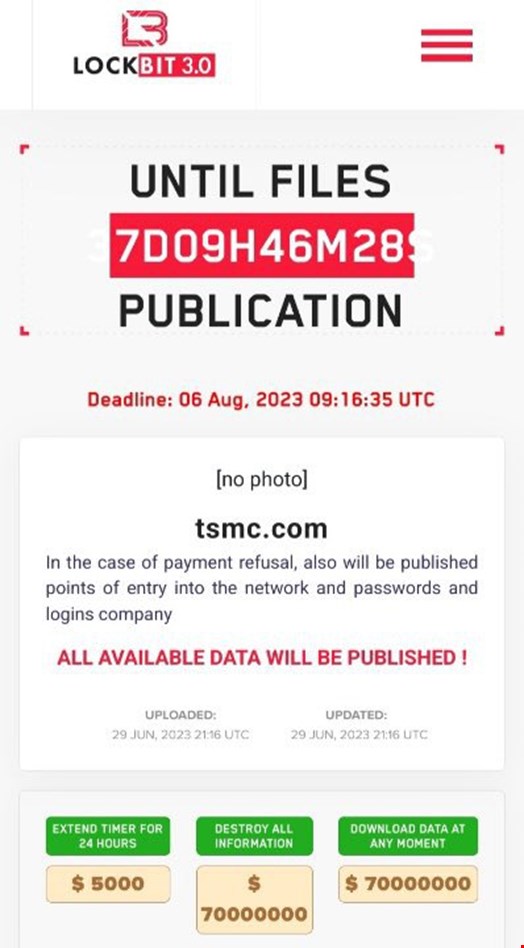
National Hazard Agency, a sub-group of the LockBit ransomware gang, posted the name of Taiwan Semiconductor Manufacturing Company (TSMC), the world’s largest chip manufacturer, on LockBit’s dark web leak site on June 29, 2023.
The threat actor has demanded TSCM pay a $70m ransom to prevent them from leaking the data they allegedly possess. The victim was initially given seven days to respond, but the deadline has since been extended to August 6.
“In the case of payment refusal, also will be published points of entry and passwords and logins company. All available data will be published [sic],” LockBit wrote.
At this stage, there is no information on the type of data LockBit may have extorted or whether they have any TSMC data at all.
At the same time it has been reported that Kinmax Technologies, one of TSMC’s suppliers – also working with Cisco, HPE, Microsoft, Citrix, VMware and Nvidia – has suffered a cyber-attack, which led to the leak of information pertinent to server initial setup and configuration.
The Kinmax has not mentioned TSMC directly and there is no official communication from the chip manufacturer at the time of writing.
If the breach is confirmed, it would be the fourth-largest ransom demand in ransomware history, according to William Thomas, a cyber threat intelligence researcher at Equinix.
Top 5 Highest Ransom Demands 📈
🔘 Hive: MediaMarkt – $240m
🔘 REvil: Acer – $100m
🔘 REvil: Kaseya – $70m
🔘 LockBit: TSMC – $70m 🆕
🔘 LockBit: Pendragon – $60mHonourable mention:
🔘 EvilCorp: CNA Financial – $40m (Paid)— Will (@BushidoToken) June 30, 2023
JD Work, a senior advisor at the US Cyberspace Solarium Commission, said on Twitter, “Lockbit claim of hit on TSMC certainly requires skepticism until extent of impact, if any, is known. But this is a good opportunity for many shops, & mission planners, to evaluate day 1 wartime scenarios.”
LockBit was recently found to be the most active ransomware group in the first quarter of 2023, according to Acronis.
TSMC produces 65% of the world’s semiconductors and 90% of the most advanced nodes. It has an estimated annual revenue of over $74bn in 2023.